Warzone's Year Activity
Description
Warzone is openly sold through a branded website, provided as malware-as-a-service for others to use in their own campaigns. As with many of these RATs, it claims to be a legitimate remote administration tool but the focus of development and guides on the site show this to be a pretence.
The RAT claims a wide range of available features on its website, including:
- Hidden RDP connection and/or remote shell for interacting with infected machines
- UAC privilege bypasses
- Webcam control
- Collection of passwords from local web browser and email clients
- File upload/download and execution
- Keylogging
- Windows Defender bypass
- Persistence
The malware uses its own DNS server to ensure reliable service, and includes a number of evasion techniques to disable Defender and gain persistence. As quoted on their website, the family includes UAC bypasses for Windows 10 and earlier versions of the OS, enabling it to elevate permissions if required.
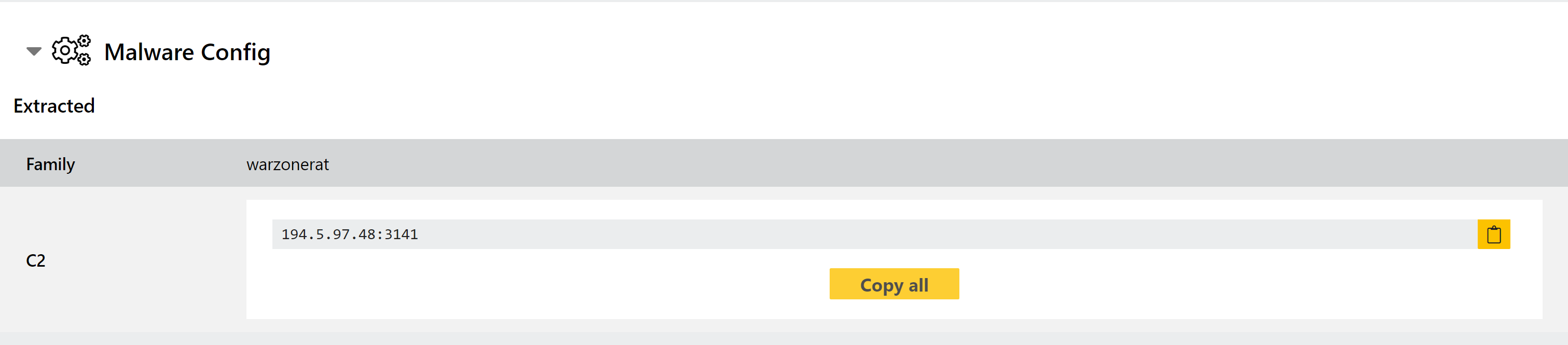
Configuration Extraction
Triage includes a configuration extractor for the Warzone family which dumps C2 information from samples during static analysis.
Common Behaiour
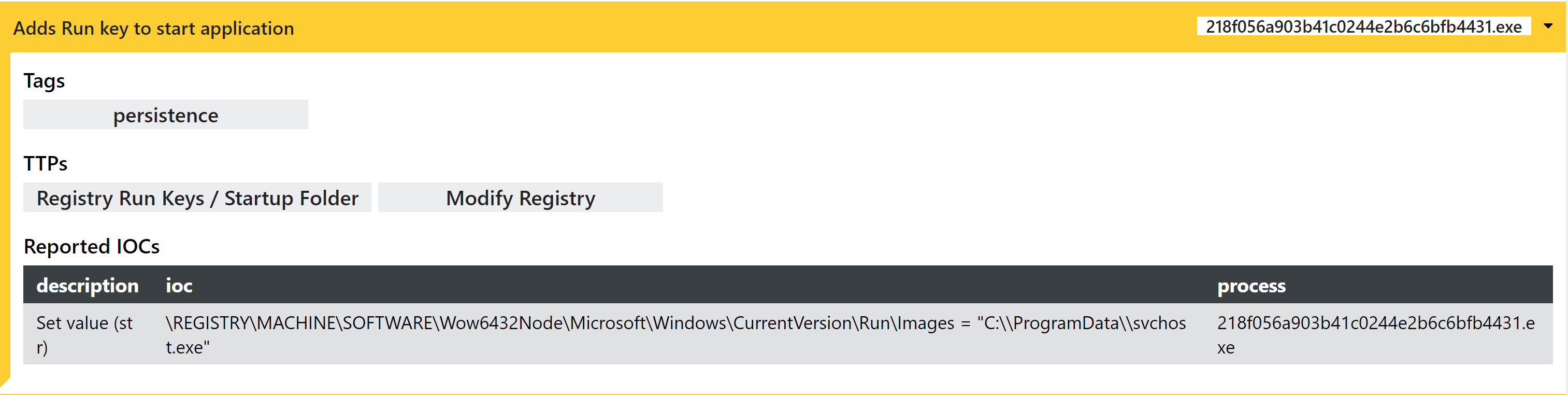
Persistence
Warzone has been observed to include a range of different persistence mechanisms in the wild depending on the version/campaign. The most common of these is a simple run key in the registry to launch the executable on system startup.
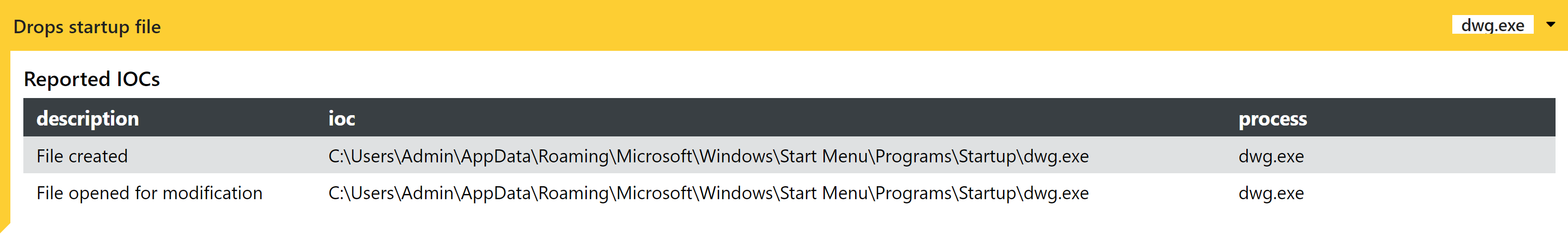
Another way it commonly launches itself on a system restart is by dropping an link to the startup folder.
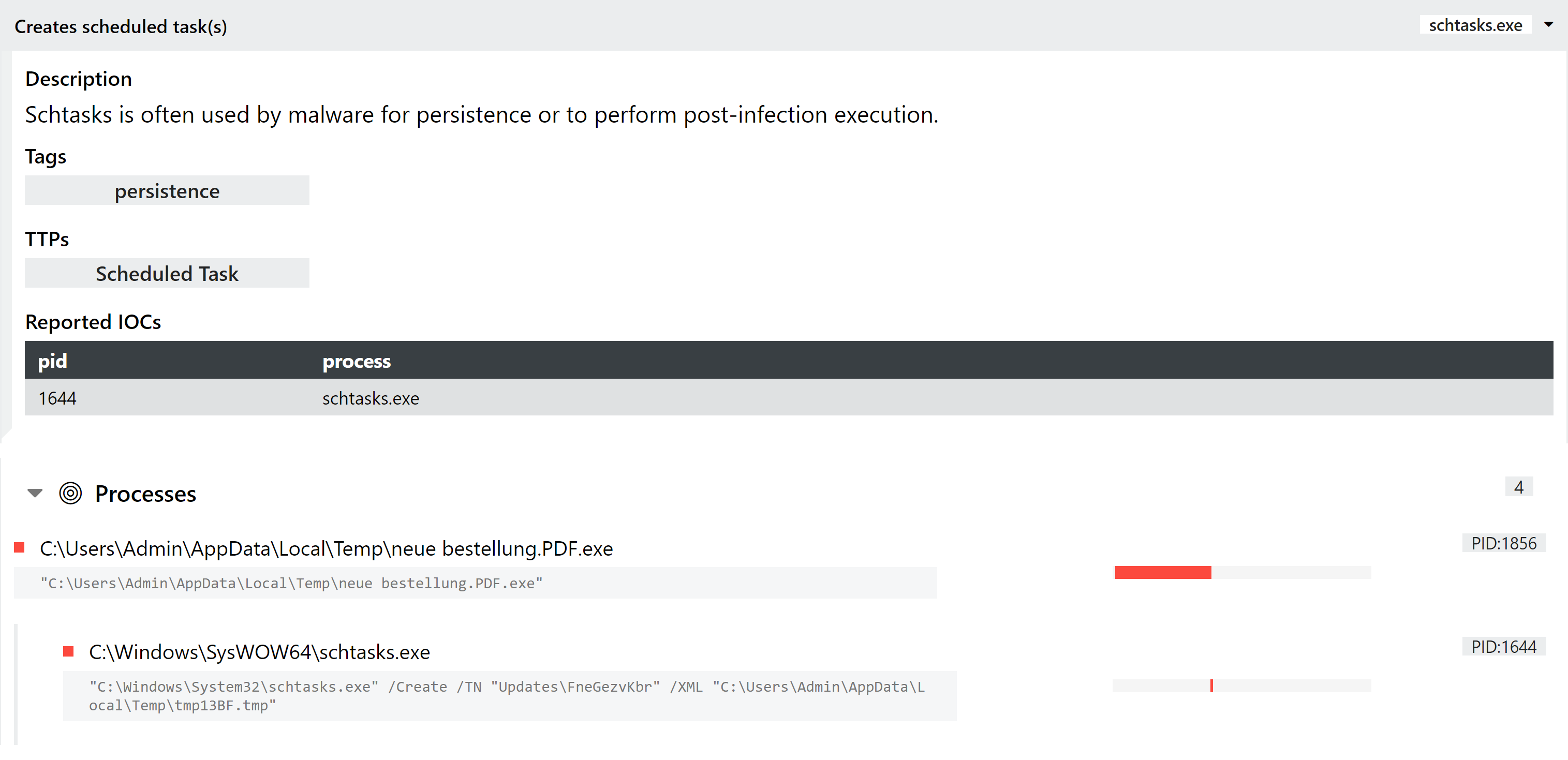
Some versions have also been observed using schtasks to create a scheduled task on the system instead.
Steals Browser/Email Credentials
As mentioned above, Warzone generally targets credentials stored locally by common web browsers and email clients. This is reported in Traige as shown below.

